Cursor Allowlist Bypass (CVE-2026-22708)
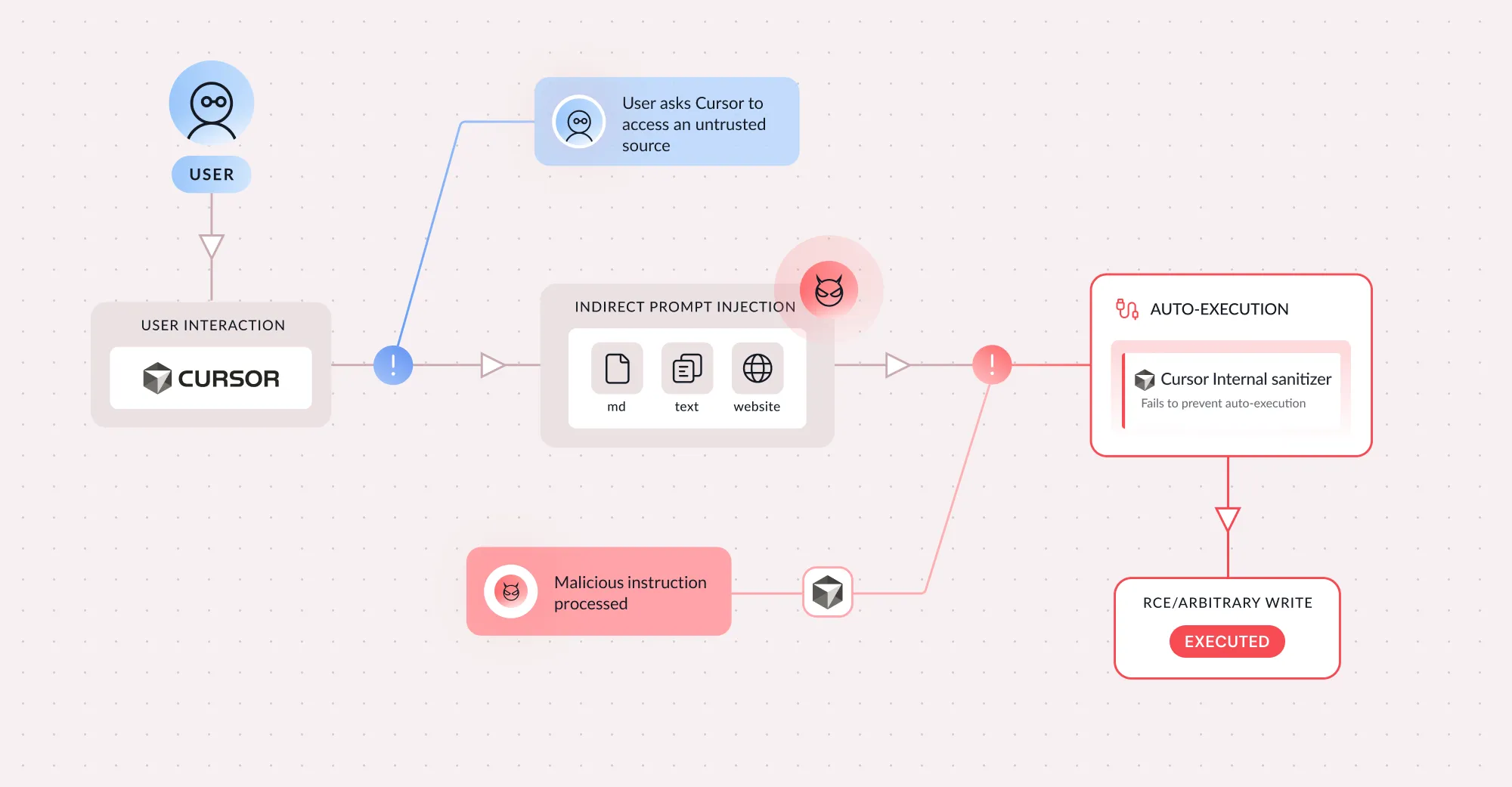
Executive Summary I discovered a critical vulnerability in Cursor (CVE-2026-22708) that exploits how agentic IDEs handle shell built-in commands. The flaw enables sandbox bypass and remote code ex...

Executive Summary I discovered a critical vulnerability in Cursor (CVE-2026-22708) that exploits how agentic IDEs handle shell built-in commands. The flaw enables sandbox bypass and remote code ex...
The guide for a freeloader Threat Intelligence Analyst and Malware Researcher Chapter Zero – Prologue Recently I saw a blog post by Trend Micro being posted in the Curated Intelligence Discord gr...
Understanding the Compound File Binary format and OLE structures to mess with CVE-2022-30190 Initially I began this research to generate weaponized RTF files delivering the CVE-2022-30190(Follina)...
Preface As part of the course we were instructed to analyze a custom malware sample developed for us, below is a full analysis of that sample plus a an automated script to extract the final payload...
Preface This week we have discussed deobfuscating initial stagers and how to unpack their executable payloads. And what I’ve decided to do, to practice this week lesson is to find actual malware o...
Preface Recently, I’ve joined @VK and @0verflows advanced malware analysis course called “Zero2Auto”. The first lesson was about algorithms in malware; compression, hashing and encryption. The firs...
Preface One day I was skimming through abuse.ch. This website collects user submitted malicious or suspicious URLs and I've stumbled through something very interesting. I saw that a user that goes ...
Finding a golden nugget in a lake full of trash For a while I was wondering, where am I going to find interesting malware? I have these huge sources of unorganized data: Malshare, VirusTotal, Virus...
Bringing the Dead back to life I would like to dedicate this post(or perhaps series of posts) to Mark Ludwig, the author of The Giant Black Book of Computer Viruses, who passed away in 2011. You’ve...
I’m afraid of no packer If you’re going to analyze malware you are going to run into packers, code injections, obfuscated code and what not. If one doesn’t possess the correct knowledge or the corr...